Everything posted by Sensei
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
@MSC My post was not directed at you.. ..."funny" thing ... you reminded me that the people who were tortured and raped at Guantanamo by the US military are now... in the government of Afghanistan... (after rethought, not funny...) (now, do you see the picture? V.P. says, you (US) did this, so I can do the same etc. etc.) An "auction" is being held as to who made the worst possible abominations..
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
...Only those who were so stupid as to make videos (and share them around the world) of them torturing and raping people... ...there were no other options... The "army" withdrawn from Kiev will go to the Donbass area, and the soldiers will be on the front line to die first, to remove the war criminals who committed the aforementioned crimes..
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
...where were you when US presidents ordered the torture of people at Guantanamo and similar facilities around the world? (I know, just look through the old threads). ...now you're complaining while the Russians are doing exactly what the US military did to innocent people.... ...V.P. said that they are doing just the same what you did.. ..but you don't even understood his words... There are war criminals from western countries.... (did you watch the movies about the US conquering the West? Indians? right?) ...and now there are war criminals from Eastern European countries... Centuries go by... same shit... ...but now broadcasted by Internet and satellites... immediately... ..and everything recorded by the Creator of The Universe... a backup version... Just in case someone lied to me in front of me...
-
Hijack from War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
..they were "frozen" because they physically did not belong to them.. i.e. "oligarchs" are just sockpuppets of V.P, like Donald T., not the real owners of the assets.. In the original thread I posted Navalny's documentary which literally nobody commented (so I assume nobody watched the video also!).. ...In which the mechanisms by which they steal money from the Russians are shown, and which are ESSENTIAL to both this thread and the parent thread... WTF is going on with you guys... You talk about "Russian oligarchs"...but you didn't even bother to check how they are connected to each other.... watch the video.... It's a bit like watching biology and evolution without mentioning genes....
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
...you skipped one essential step: asking them what they think of Russia's attack on Ukraine, i.e., whether they personally support mass murder, or they reject the "official propaganda"... Some countries, stores, businessmen have already started to do this on their own, i.e. Russians who want to make deals with them have to sign documents condemning the aggression of the V.P. and the Russian army against Ukraine.. It should be extended to all Russians who want to visit the EU, US or any other Western country..
-
how to test battery of a vehicle
I would connect an ammeter between one of the battery electrodes and the cable to see if current is flowing there. If so, it means something is draining the battery overnight. Energy = Current (from multimeter configured as ammeter i.e. serial, which requires disconnection of battery, and plugging multimeter like above) x Voltage x Time (in Joules). Divide by 3600000 to get it in kWh.
-
Why do we use CMYK color for printing?
Professionally this should be called: dithering. https://en.wikipedia.org/wiki/Dither Dithering is also used in ordinary TrueColor, 24 bits, 16 mln (16777216), color computer graphics. From black 0,0,0 to white 255,255,255 there is just 256 shades of gray. If gradient covers large area of the screen, e.g. 1920 width, bands of similar shade are clearly visible (1920/256 = 7.5 pixel). To simulate more colors dithering is used, to exceed 16 mln colors range.
-
Physics of video games
Looks pretty straight forward to me. Each object has a x,y or x,y,z location. Each object has a velocity vector vx,vy or vx,vy,vz. Each object has an acceleration vector ax,ay or ax,ay,az. And there is general g acceleration downward (y). d=1/2*a*t^2 is general equation of how far object will fly with given acceleration, after t seconds. So, you add it to character position, and just animate acceleration vector. e.g. user presses left or right arrow to move character, you change ax accordingly, user presses jump, you change ay vector, and the main routine (executed to update every frame of the game), based on it, modifies vx,vy[,vz] and they modify x,y[,z]. Then you do collision detection, to see if character or object can be moved in such direction or not. https://en.wikipedia.org/wiki/Collision_detection#Video_games Show code of your game.
-
problem with connecting with mysql
Use: SHOW VARIABLES LIKE 'validate_password%'; to learn what is validate_password_policy value. Then set it by: mysql> SET GLOBAL validate_password_policy=LOW; OR mysql> SET GLOBAL validate_password_policy=0; Then you should be able to set low quality passwords for new users (not recommended for a real server).
-
problem with connecting with mysql
@zak100 https://www.google.com/search?q=ERROR+1819+(HY000)%3A+Your+password+does+not+satisfy+the+current+policy+requirements
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
...people always say that.. that things were better in the past days.. (mostly because they have no idea)
-
Badges in Scienceforums.net
..there is very special badge for somebody who will get in bunker where is hiding enemy of the world (aka "V.P.")..
-
Validity of the claim that Will Smith "could've killed" Chris Rock
..I already know what they will be joking about at the next 10+ Oscars.. Don't slap the presenter.. ..or the next presenter will be Arnold S. (he wouldn't dare make such a joke in the first place), or Jean Claude van Damme.. ..or they will "hire" Jean Claude van Damme as bodyguard (enough funny!), to "protect the presenter against slappers".. (then the presenter will start mocking of Jean Claude van Damme.. and the answer will be: "I'm a professional at work, I can't kick his ass on air, but the broadcast won't last forever".... )
- Political Humor
-
URL shorteners
A list of URL shorteners can be found here (incomplete list): https://www.google.com/search?q=URL+shorteners+list Basically, the idea is to have as few characters as possible in the domain name (e.g., instead of google.com it's goo.gl) and as few characters as possible in the path (i.e., immediately following the hostname are letters and numbers that make no sense to humans). Full URLs are detailed because of the way search engines work. Therefor webmaster SEO (Search-Engine Optimizations) tend to put important search-engine keywords into URLs. Like the full title of the article with all the details of the thread being discussed. e.g. website selling electronics, 3d printers with brand XYZ, with model ABC, want to generate URL with format like: https://www.example.com/products/3dprinters/XYZ/ABC/ (which is usually handled by rewrite-engine https://en.wikipedia.org/wiki/Rewrite_engine at HTTP web server level, and converted to internal query-string)
-
URL shorteners
Depends. If you have a link such as: https://www.example.com/article?id=1234&uid=19182737774902&[.......] The id is the article identifier, which is an essential argument to the script, so it cannot be removed. So after deletion, the new link will look like: https://www.example.com/article?id=1234 If you have a link such as: https://www.example.com/article/1234?uid=19182737774902&[.......] The id of the article is integrated with path part (which might be just an illusion given by rewrite-engine) So after deletion, the new link will look like: https://www.example.com/article/1234 Should be okay. After clearing the URI/query-string portion before sharing, try the new URI string in a private browser session to see if the link still works.
-
URL shorteners
Part after "?" is called query-string. https://en.wikipedia.org/wiki/Query_string ...if you received an "interesting link that you want to share with someone".... you should ALWAYS remove tracking data from the query-string, whether you send it to a family member by mail, text message, or provide it on a forum in raw form or shortened by URL shorteners.
-
URL shorteners
?? You're thinking about query-string arguments? Domain A (e.g. the JS script hosted on it) creates cookie/supercookie if it is not present ("session id"). Website X uses the code from domain A (cookie/supercookie is set to initial value). X has link to Y. The user goes from X to Y (a reference URL is sent with it, so Y knows who referred it). Website Y does not use the code from domain A. The user goes from Y to Z (a reference URL is sent with it). Website Z uses the code from domain A (cookie/supercookie is already sent). "A" knows that you visited X, Z directly from analyze of the logs.. because the same cookie/supercookie is found..
-
problem with connecting with mysql
Worth a try: https://stackoverflow.com/questions/1720244/create-new-user-in-mysql-and-give-it-full-access-to-one-database i.e. create a new user and give privileges (if you haven't already done so).
-
problem with connecting with mysql
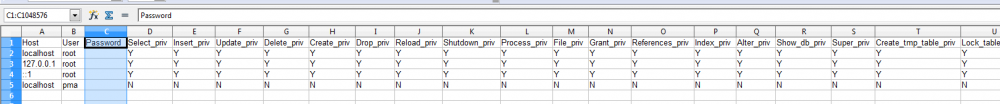
Copy it into a text editor that allows horizontal scrolling, and you'll see it's not garbage. I am working on Windows and using XAMPP. The differences between what I have here and what you have are small. I have a "Password" column that is blank in all rows, which is not in your log... I have multiple "root" user accounts, each for IPv4 and IPv6, either by name or directly by IP number. Have you tried the phpmyadmin from a web browser? Different MySQL versions can behave slightly differently. So if I were you, I would try inserting a password column in mysqladmin/phpmyadmin, and then duplicate the row to have IPv6 support as well, just in case. Just like in my screenshot above.
-
problem with connecting with mysql
What you get when you use: select * from mysql.user; ? Has this ever worked with Python, or is this your first time using MySQL with your own Python code? BTW, careful with "localhost". "localhost" on machines with enabled IPv6 can mean ::1, otherwise 127.0.0.1 e.g. if I in command-line use ping localhost, I see it resolves to ::1 Windows firewall checked/disabled?
-
Why cant they invent a computer program that solves the energy crisis in mathematical terms?
..but it is very easy to solve.. simply all people on the entire planet must stop using money (in any form).. Apart from physical limits, availability of money prevents scientists, engineers, workers, anybody from doing something.. NASA engineers after shutdown of Apollo program did not "forget" how to build rockets. The US government cut them from money, and dismissed high-level knowledgeable and sent them home, have to go to work in the private sector, below their abilities. If you have "economy" without money, you can build solar panels at any quantity, limited just by speed of getting rare chemical elements from mines required to build them. In a "classic", i.e. today's economy, if people won't buy e.g. solar panels by themselves, they won't have them (there is need one of on each building or so).. Some Western countries governments are trying to speed this up by giving refunds (fixed amount, 25%, 50%, 100%) for buying devices producing renewable energy, but it's a huge bureaucracy, and method of stealing money before it gets to the average Joe Doe, and the refund is given after the device is already on the building, so people still have to have that money up front)... So basically, if someone isn't rich, someone isn't eco-friendly, they'll just skip the crap offer from the government.. Governments should "own" the solar panel manufacturers, installation companies, etc., otherwise when demand for the product increases, the private sector will simply raise the price for the product and installation costs (basically sucking up all the tax money).
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
https://en.wikipedia.org/wiki/Millerovo_air_base_attack @zapatos
-
War Games: Russia Takes Ukraine, China Takes Taiwan. US Response?
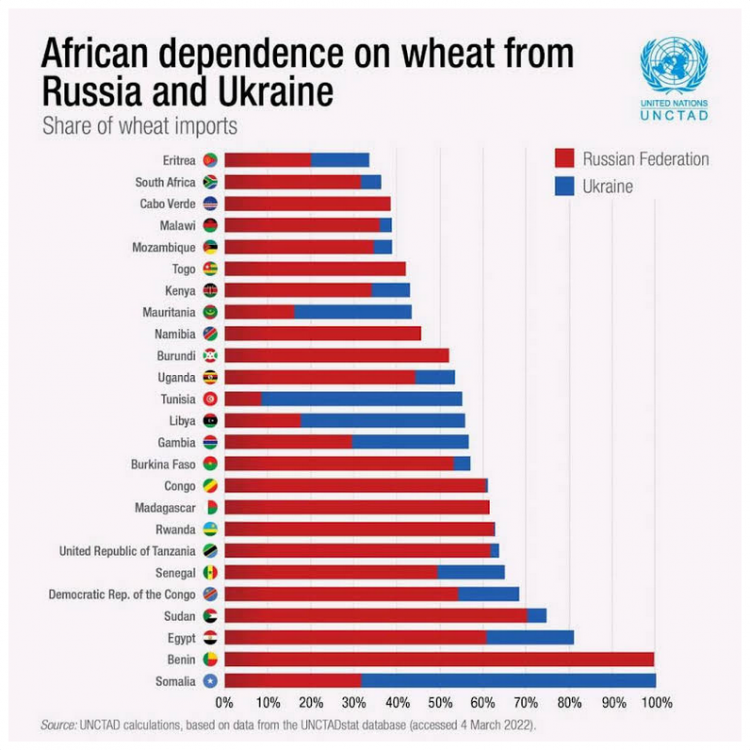
Due to the war, these countries may experience food problems in just a few months: https://www.voanews.com/a/ukraine-war-to-compound-hunger-poverty-in-africa-experts-say/6492430.html "Experts warn the war in Ukraine could increase hunger and food insecurity for some people in Africa. Most African countries import wheat and vegetable oil from Ukraine and Russia, a region now engulfed in conflict since Russia invaded its neighbor." "The United Nations says Russia and Ukraine produce 53% of the world’s sunflowers and seeds, and 27% of the world’s wheat." "The study shows at least 25 African countries import a third of their wheat from Russia and Ukraine, and 15 of them import more than half from those two countries." https://www.gonewsindia.com/latest-news/international/african-arab-countries-food-dependence-on-russia-ukraine-28571
-
Is there any program that can convert letters to numbers and/or words into sums thereof?
If it is not for numerology, but to check integrity (e.g. if somebody altered content) why not to use hash? On Windows there is built-in certutil command which can calculate MD5, SHA1, SHA256 hash-functions. https://www.google.com/search?q=certutil+hashfile https://en.wikipedia.org/wiki/SHA-2 If you calculate hash-function of some word, sentence, file or entire disk, you can be pretty sure to 99.99% when you see the same hash, it's the same object. echo "string" | sha256sum on Linux will give you hash of string, instead of a file. Hackers/programmers/people use it to check if someone has broken into their computers by running it in Linux on all storage: https://www.google.com/search?q=md5sum+linux https://www.google.com/search?q=md5sum+linux+entire+directory If you want to know if someone has changed the MBR of your Linux system you are using e.g. dd if=/dev/sda iflag=direct bs=512 count=1 2>/dev/null | sha256sum To verify the entire first partition of the first disk: dd if=/dev/sda0 iflag=direct bs=16M 2>/dev/null | sha256sum If it is so simple algorithm as you wrote, you will get the same sum after letters are replaced.. "abc" will give the same as "cab"..